Scenario 2
Java Applet to Sybase Database with Security Bypass
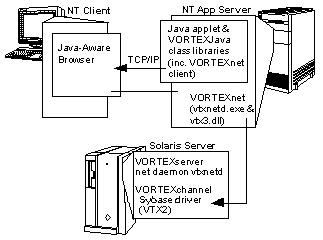
In Scenario 2, a Sybase database server provides data to a client running
a Java applet application server. This configuration requires network
hopping to bypass the Java security feature that limits socket access to
the machine from which the applet was loaded.
This scenario can also be used to get through a firewall.
The components, URLs, user names and
passwords are all examples. You must substitute the correct values for
your own site.
Components
Client
»
VORTEXjava as part of applet.
»
connection call for db.connect():
db.connect("mysrv",1958,"/usr2/trim/bin/vtxhost.net",
"sa/sa/master2@1958:mysyb!/usr2/trim/bin/vtxhost.syb,SYBASE=/usr/sybase","");
Client serving as application server and network hopper
»
machine name: mysrv
»
machine operating system: Solaris
»
VORTEXnet
Server
»
machine name: mysyb
»
machine operaing system: Solaris
»
Sybase userid: sa
»
Sybase passwd: sa
»
Sybase dbname: master2
»
Sybase home: /usr/sybase
»
VORTEXnet
Sequence
- Set the SYBASE environment variable to /usr/sybase.
- The VORTEXnet evaluation kit, which includes the daemon and driver,
is installed in /usr2/trifox/bin on both mysrv
and mysyb.
- The VORTEXdaemon, vtxnetd, is started on mysrv and mysyb as follows:
vtxnetd -p1958 &
- When db.connect(), a message is sent via the socket (port 1958) to
vtxnetd on mysrv to start up vtxhost.net.
- vtxhost.net is given the service string
sa/sa/master2@1958:mysyb!/usr2/trim/bin/vtxhost.syb,SYBASE=/usr/sybase,
which tells it to send a message via the socket (port 1958) to vtxnetd on
mysyb to start up vtxhost.syb.
© 1985-2025
Updated 26 Sep 2005.
|
![[LOGO]](/img/logo.gif)
![[Navigation Map]](/img/combo.gif)
![[LOGO]](/img/logo.gif)
![[Navigation Map]](/img/combo.gif)